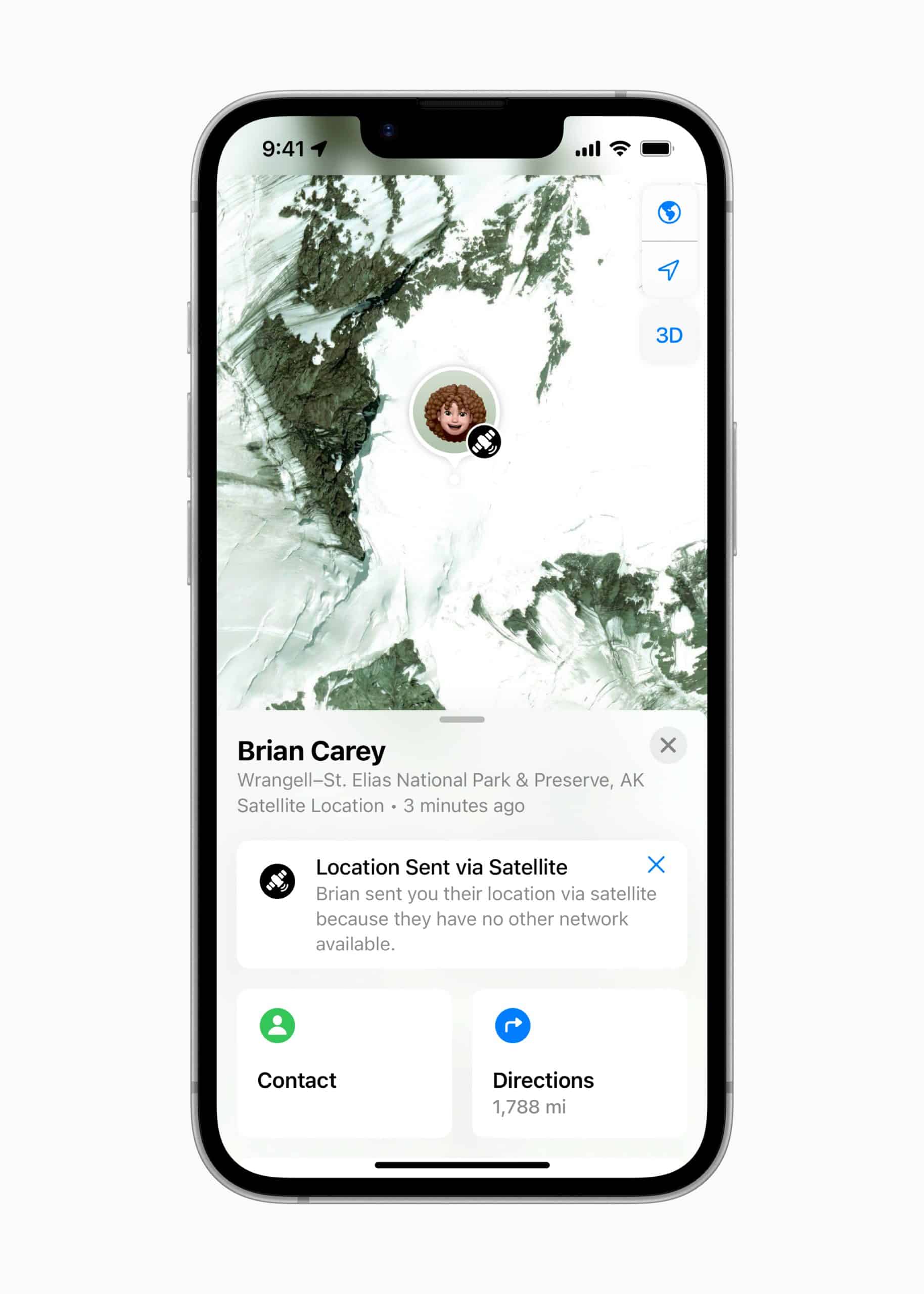
The Find My network is a critical part of Apple’s infrastructure, enabling users to track devices like iPhones, iPads, Macs, AirPods, and AirTags. By leveraging millions of Apple devices worldwide, the system allows lost items to be located even when they are offline.
- Crowdsourced Tracking: Apple devices nearby anonymously detect lost devices and relay their location.
- Encrypted Communication: Location data is end-to-end encrypted, ensuring that only the device owner can access it.
- Offline Tracking: Even if a device is not connected to Wi-Fi or cellular data, it can still be located using Bluetooth signals detected by other Apple devices.
These features make the Find My network a powerful tool for users—but also a potential target for security vulnerabilities.
Details of the Find My Network Security Exploit
The newly discovered Find My network security exploit appears to take advantage of weaknesses in how location data is transmitted and processed within Apple’s network. While the exact technical details remain undisclosed to prevent malicious use, security researchers have identified potential risks.
- Unauthorized Tracking: Attackers could potentially exploit the system to track devices without user consent.
- Data Interception: Despite encryption, vulnerabilities in implementation could expose location data.
- Exploiting Lost Mode: The exploit might allow bad actors to manipulate how lost devices are tracked or retrieved.
These risks highlight the need for continued scrutiny of security protocols within Apple’s location-tracking network.
How This Exploit Could Be Used in Real-World Scenarios
Security flaws in device-tracking technology can be exploited in various ways, raising concerns for both individual users and organizations.
1. Unwanted Tracking and Stalking Risks
- Attackers could use the exploit to bypass Apple’s anti-stalking protections and track individuals without their knowledge.
- Previous incidents involving AirTags have already highlighted concerns about unauthorized tracking.
2. Device Theft and Countermeasures
- Thieves could manipulate the Find My network to interfere with tracking lost or stolen devices.
- If attackers find a way to disable tracking remotely, stolen devices could become more difficult to recover.
3. Potential for Corporate Espionage
- Organizations using Apple devices may face risks if their assets can be tracked or monitored without authorization.
- Sensitive business locations could be compromised through unauthorized tracking.
These potential scenarios emphasize the need for Apple to address and mitigate any weaknesses in the Find My network.
Apple’s Response to Security Vulnerabilities
Apple has a strong track record of addressing security flaws quickly, often releasing software updates to patch vulnerabilities as they are discovered. While the company has not yet publicly acknowledged this specific Find My network security exploit, it is likely working on a fix.
- Rapid Patch Deployment: Security updates are frequently rolled out via iOS, iPadOS, and macOS updates.
- Bug Bounty Program: Apple rewards security researchers for discovering and responsibly disclosing vulnerabilities.
- Encryption Standards: End-to-end encryption remains a cornerstone of Apple’s security approach.
Apple is expected to release an update that addresses the exploit while maintaining the usability of the Find My network.
How Users Can Protect Themselves
While Apple works on a solution, users can take steps to minimize risks associated with potential exploits in the Find My network.
1. Keep Devices Updated
- Regularly updating to the latest iOS, iPadOS, or macOS version ensures security patches are applied.
2. Monitor Find My Activity
- Check the Find My app regularly for any unusual devices linked to an account.
3. Disable Find My When Not Needed
- If users suspect a security issue, temporarily disabling Find My can prevent potential unauthorized tracking.
4. Enable Security Notifications
- Apple provides notifications if an unknown AirTag or device is tracking a user’s location.
These proactive steps help reduce the risk of falling victim to location-tracking exploits.
The Broader Implications of Location-Tracking Security
The discovery of a Find My network security exploit is part of a larger discussion about the balance between privacy and convenience in device-tracking technology.
- Consumers expect robust tracking features, but they also demand strong privacy protections.
- Governments and regulators are increasingly scrutinizing how tech companies handle location data security.
- Previous cases of AirTag misuse have led Apple to introduce anti-stalking features.
- Other companies, including Google and Samsung, have faced similar security concerns with their tracking technologies.
As location-tracking technology evolves, companies must remain vigilant in securing user data.
What This Means for the Future of Find My
Apple’s Find My network is one of the most advanced device-tracking systems available, but any security vulnerability can undermine user trust.
- Enhanced Encryption: Apple could strengthen encryption protocols to prevent data interception.
- Stronger Anti-Tracking Features: Additional safeguards may be introduced to protect against unauthorized tracking.
- Improved Lost Mode Security: More robust measures to prevent bad actors from manipulating lost device recovery.
Apple’s ongoing investment in security will determine how effectively it can address emerging threats while maintaining the functionality of the Find My network.
Final Thoughts on the Find My Network Security Exploit
The discovery of a Find My network security exploit highlights the complexities of securing location-tracking technology. While Apple has built one of the most secure tracking systems available, no system is entirely immune to vulnerabilities.
As Apple investigates and responds to this issue, users should stay informed, update their devices, and follow best practices for securing their data. With the right balance of security and usability, Apple can continue to provide a reliable and trusted tracking solution for millions of users worldwide.